A recent Statista report estimates that the Robotic Process Automation (RPA) market will be valued at 81.8 billion U.S. dollars by 2032. Additionally, Gartner highlights that RPA remains the second-fastest growing segment within the AIM market, boasting a growth rate of 22%.
What does this data signify?
It clearly indicates that RPA adoption is unstoppable. Various industries are integrating RPA as a crucial element of their digital transformation initiatives.
However, this widespread adoption raises critical questions for business leaders:
Is RPA adoption safe?
The importance of RPA security cannot be overstated. Securing your RPA project is vital to protect sensitive data, ensure compliance, and mitigate potential risks that could negate the benefits of automation.
In this blog, we will:
-
- Explore the importance of RPA security
-
- Identify challenges in RPA security
-
- Discuss best practices for RPA security
What is RPA Security?
RPA security encompasses the measures and protocols implemented to safeguard automated processes and the data they handle. This includes securing RPA tools, platforms, and the interactions between bots and other systems. Key components of RPA security involve access controls, data encryption, monitoring, and compliance management.
Why RPA Security Matters?
RPA is being leveraged across various industries to enhance productivity and operational efficiency.
And the rise of RPA implementation brings with it concerns about its security challenges. Since RPA systems interact with multiple applications, databases, and sensitive information, they become prime targets of bad actors. A breach in RPA security can lead to unauthorized access to critical systems, and data leaks.
Importance of RPA Security
-
- Protection of Sensitive Data: RPA systems often handle sensitive and confidential data, including customer information, financial records, and intellectual property. Without proper security measures, this data is vulnerable to breaches.
-
- Compliance with Regulations: Many industries are subject to stringent data protection regulations (e.g., GDPR, HIPAA). Ensuring RPA security helps organizations comply with these laws, avoiding legal repercussions and hefty fines.
-
- Maintaining Business Continuity: A security breach in RPA systems can disrupt business operations, leading to downtime and loss of revenue. Robust RPA security measures ensure continuity and reliability.
-
- Preserving Organizational Reputation: Data breaches can severely damage an organization’s reputation. Investing in RPA protection helps maintain customer trust and brand integrity.
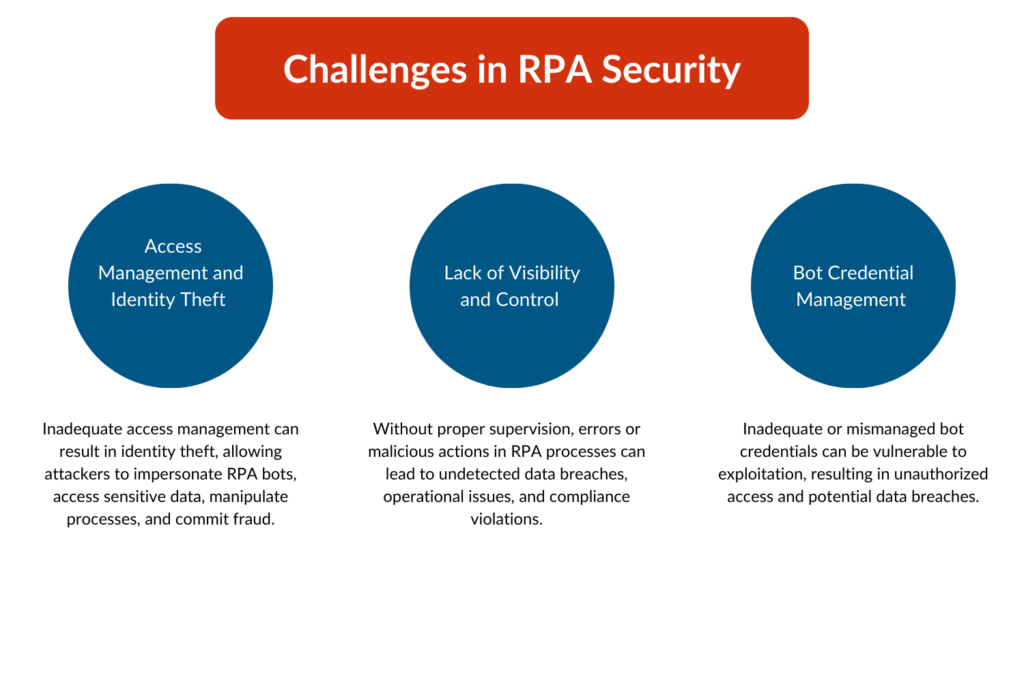
Challenges in RPA Security
Despite the benefits of RPA, securing these systems presents several challenges. Understanding these challenges is the first step in implementing effective RPA protection strategies.
1. Access Management and Identity Theft
One of the primary security concerns with RPA is access management. RPA bots typically require access to multiple systems and applications, often using credentials similar to those of human users. If these credentials are not managed properly, they can be exploited by malicious actors.
Poor access management can lead to identity theft, where attackers use stolen credentials to impersonate RPA bots. This can result in unauthorized access to sensitive data, manipulation of automated processes, and fraudulent activities.
2. Lack of Visibility and Control
RPA systems that operate in the background, often without direct human supervision lacks visibility, making it difficult for organizations to monitor and control bot activities. This may increase the potential risks of undetected security breaches.
Without proper oversight, malicious activities or errors in RPA processes can go unnoticed, leading to data leaks, process failures, and compliance violations.
3. Bot Credential Management
RPA bots require credentials to access the systems and applications they automate. Managing these credentials securely is a significant challenge, especially when dealing with a large number of bots.
Weak or poorly managed bot credentials can be easily exploited, leading to unauthorized access and potential data breaches.
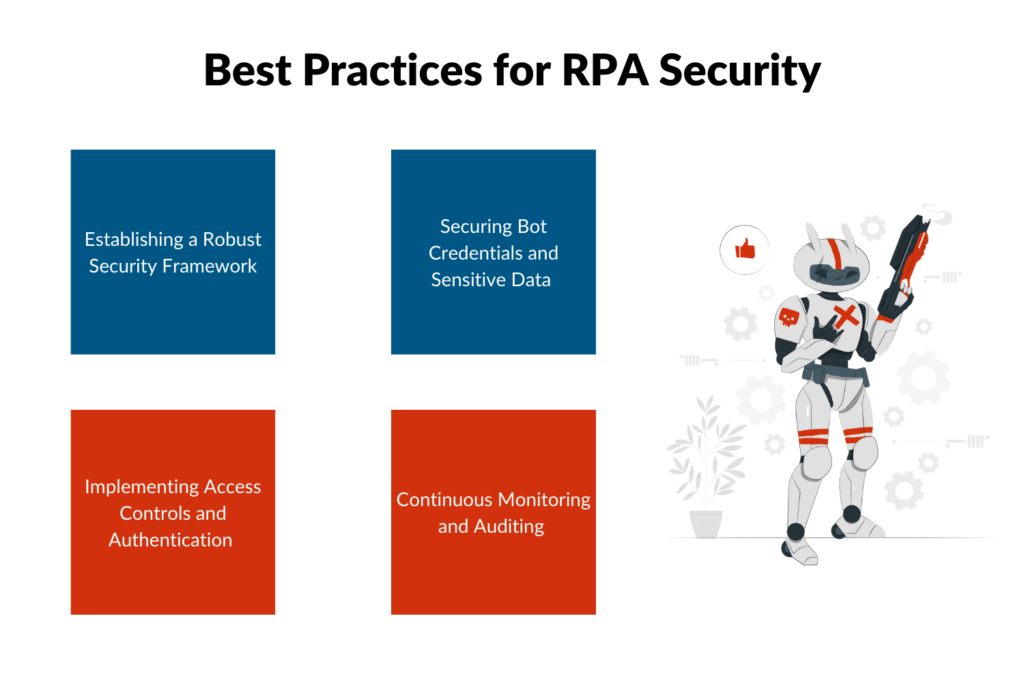
Best Practices for RPA Security
1. Establishing a Robust Security Framework
Developing a Comprehensive RPA Security Policy: A detailed security policy should outline the security measures, protocols, and responsibilities associated with RPA. This policy should be regularly reviewed and updated to address emerging threats.
Regular Risk Assessments and Security Audits: Conducting regular risk assessments helps identify potential vulnerabilities in RPA systems. Security audits ensure that these vulnerabilities are addressed and that the RPA environment complies with relevant regulations.
2. Implementing Access Controls and Authentication
Role-Based Access Control (RBAC): Implementing RBAC ensures that bots and users have access only to the data and systems necessary for their roles, reducing the risk of unauthorized access.
Multi-Factor Authentication (MFA) for Bot Access: MFA adds an extra layer of security, ensuring that only authorized personnel can access and control bots.
3. Securing Bot Credentials and Sensitive Data
Encryption of Data in Transit and at Rest: Encrypting data ensures that even if it is intercepted, it cannot be read without the encryption key. This applies to data handled by bots and stored in databases.
Secure Storage and Management of Bot Credentials: Using secure vaults or credential management systems to store bot credentials can prevent unauthorized access and ensure that credentials are rotated regularly.
4. Continuous Monitoring and Auditing
Real-Time Monitoring of RPA Activities: Implementing real-time monitoring helps detect anomalies and potential security incidents as they occur, allowing for immediate response.
Regular Audits and Compliance Checks: Regular audits ensure that RPA processes comply with internal policies and external regulations. Compliance checks help identify areas for improvement and ensure that security measures are effective.
Conclusion
RPA Security is paramount for businesses to fully realize the benefits of automation while protecting sensitive data and ensuring compliance. By understanding the challenges and implementing best practices, organizations can effectively secure their RPA processes. A robust security framework, access controls, encryption, and continuous monitoring are essential components of a comprehensive RPA security strategy. As the RPA landscape continues to evolve, staying ahead of emerging threats and leveraging new technologies will be critical for maintaining RPA security.
Organizations must prioritize RPA security and take proactive measures to address potential risks. By doing so, they can harness the full potential of RPA while safeguarding their data and operations.